MTI Journal
MTI Journal.13
Maritime Cybersecurity
– New Area of Safe Operation –
Takuya Makiyama
Researcher, Maritime and Logistics Technology Group*
*The job title is as of August 11, 2020
Since May 2019, I have been loaned to MTI from a private think tank and am engaged in improving the Information and Communication Technology (ICT) infrastructure for developing maritime IoT. At the think tank, I specialized in ICT but had no connection with the maritime industry then. At MTI, I had wide and fresh experiences, e.g., researching the condition of satellite communication by visiting a ship or being engaged in rulemaking processes in the maritime industry. I learned how to create values from investigation and research through the experiences; the operational process at an actual site was actually changed or a guideline in the industry was established based on my investigation and research results. At MTI, I have continuously worked on cybersecurity as one of my R&D themes. For the past year and more, I have been involved in research on cybersecurity aboard ships.
Background ~Risks of Cyberattacks to Ships Are Increasing~
For a long period, ships had been considered resistant to cyberattacks because the communication with land is limited and the connections between the onboard equipment and systems were also sparse. However, with the development of satellite communications, ships have become constantly connected to the Internet. As a result, data-collection equipment has become connected to onboard equipment and systems as a hub, and data sharing between ships and land has increased sharply for utilization such as monitoring ship-operation data on land.
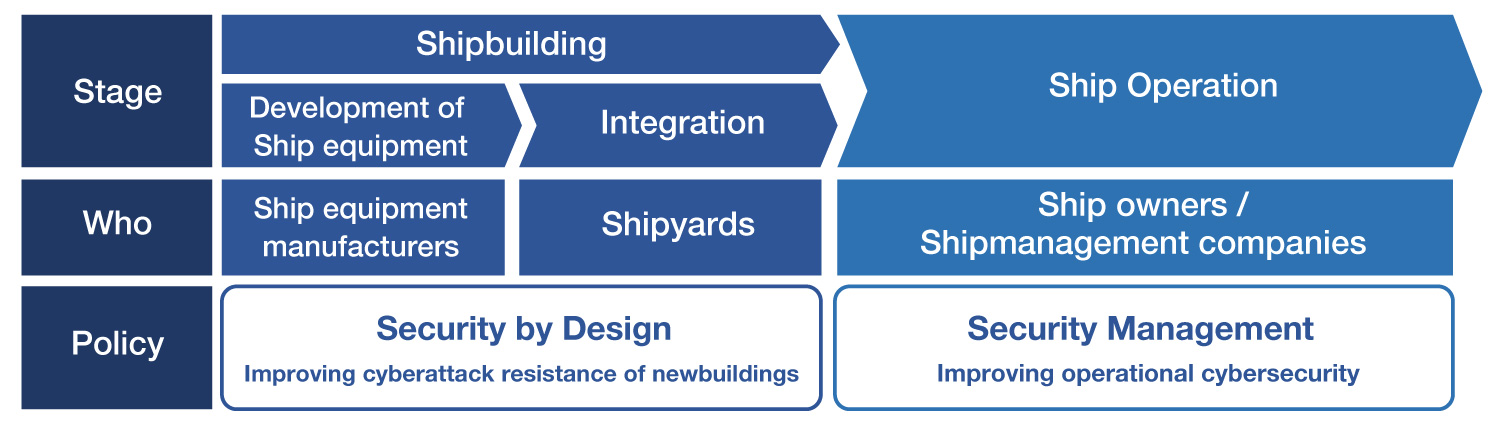
While the utilization of data is improving operational efficiency, the possibility of being cyberattacked is increasing. Cyberattacks on ships are a huge risk, as they can have tragic consequences such as grounding and collisions with other ships. Of course, the maritime industry isn’t just sitting idly but is starting to improve ship cybersecurity. The activities can be divided into security management and security by design depending on which stage of the shipping value chain (shipbuilding, ship operation) is targeted. In the following, I will introduce the trends of the entire industry and NYK and MTI’s efforts from the perspectives of security management and security by design.
Difference between security management and security by design
Security Management ~Improving Operational Cybersecurity~
Security management is a general term for efforts to improve cybersecurity in terms of operation during ship operations. As an industry-wide move, a resolution on maritime cyber risk management was adopted at the 98th session of the IMO Maritime Safety Committee (MSC) in June 2017. As a result, shipowners and operators are recommended to implement the cyber risk management utilizing a safety management system (SMS) based on the international safety management (ISM) code by the first annual inspection after January 1, 2021. In response to this resolution, classification societies in each country have established cybersecurity-related rules and guidelines for ship operations.
To respond to this movement, NYK and MTI, as an operator, are working to improve operational cybersecurity. Specifically, the SMS manual describes cyber risk management and has been certified by the Nippon Kaiji Kyokai.1 From the perspective of “compliance with IMO rules,” it is sufficient to establish cyber risk management policies and procedures, but to effectively improve cybersecurity, the procedures must be operated properly at the actual sites – and ship management companies are in charge of operations at the actual sites.
In 2019, I visited NYK Shipmanagement Pte Ltd. (NYK SM), a ship management company in Singapore with related staff members, and we held a workshop for improving operational cybersecurity at actual sites. A specialist of cybersecurity, a member of NYK’s Marine Group, and an ICT department manager joined the workshop and discussed the required operation and the opinion of the actual site. Through the workshop, we were able to support vessels managed by NYK SM to thoroughly implement cybersecurity measures.
Consequently, we would have some inconvenience, e.g. PCs that MTI mounts on ships for R&D must comply with far stricter cybersecurity rules than ever. So to speak, the utilization of ICT is the accelerator, and cybersecurity is the brake. As an R&D company, MTI is promoting the utilization of ICT while working on cybersecurity, so I think that we are uniquely positioned to realize the good balance between accelerator and brake.

When visiting Singapore for holding the workshop (author is in the center)
Security by Design ~Improving Resistance to Cyberattacks on Newbuildings~
There is a limit to improving operational cybersecurity. For example, if there are lots of loopholes in the onboard network, or if equipment vital to ship operation is mixed with relatively unimportant equipment in the same network, it is difficult to prevent and early respond to cyberattacks in terms of operation. So, if cyberattack resistance is not taken into account from the designing phase, it cannot be a fundamental solution. Considering cyberattack resistance from the ship-design phase like this is called security by design. As an industry-wide movement, in May 2020, the International Association of Classification Societies (IACS) announced a recommendation on improving the resistance of newbuildings to cyberattacks. In the future, major classification societies will develop guidelines and verification systems for cyberattack resistance of newbuildings based on this document.
Marine equipment manufacturers and shipyards are mainly working on security by design, but the NYK Group is also actively involved in the rulemaking. It would be unfortunate if a ship were built whose cyberattack resistance was high but inconvenient for the ship operator. To avoid such trouble, it is important that users (shipping companies) be involved in the rulemaking. In addition, the shipping companies’ involvement as customers could accelerate the activities of marine equipment manufacturers and shipyards.
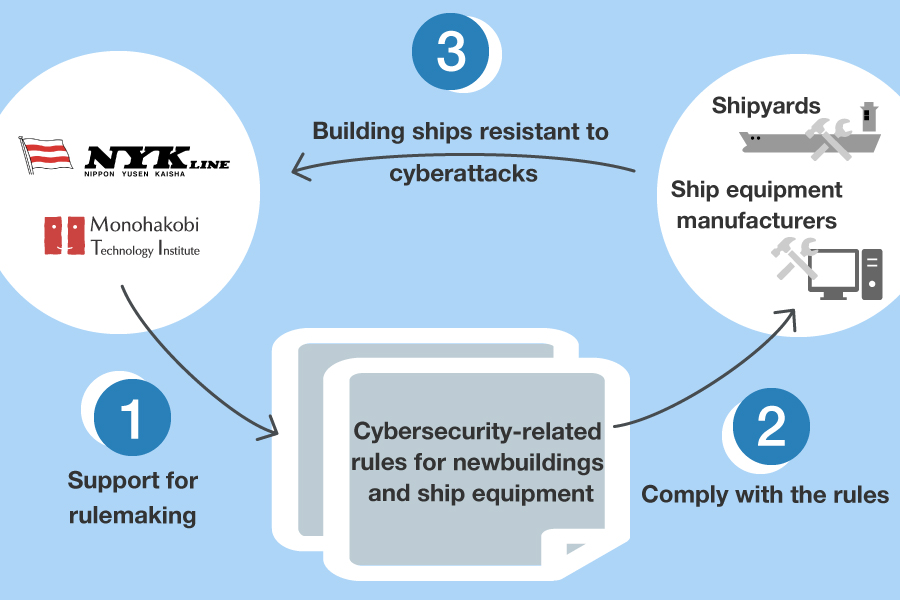
Aiming for the Improvement of Cybersecurity for the Whole Life Cycle of Ships
Considering the progress in the utilization of ICT for ships, I believe that cybersecurity will be more and more important in the future. For the NYK Group, to ensure safe operation, which is the premise of the value provided by shipping companies, investing in cybersecurity will be essential. As you can see from the two concepts just introduced – security management and security by design – cybersecurity relates to the whole life cycle of ships. But at present, the entity responsible for cybersecurity changes at each stage of shipbuilding and operation, which inconstancy will be a significant issue for the future.
MTI is a unique company, where researchers with backgrounds involved in the shipping value chain, such as shipping companies, shipyards, and marine equipment manufacturers, gather. That peculiarity will be a great advantage when considering cybersecurity with an eye on the entire ship life cycle. The following penetration test2 of onboard equipment systems might be a good example. In addition to a shipping company and shipyards and ship-equipment manufacturers, an IT company, NTT Data, also joined and cooperated to verify the cyberattack resistance of onboard equipment systems. When the test was conducted this time, it assumed the shipbuilding stage, but future tests may be required to verify the actual resistance to cyberattacks at all stages of a ship’s life cycle. In anticipation of the future, MTI should take advantage of its peculiarities and proactively engage in rulemaking and demonstration tests.
2 Penetration test: an authorized simulated cyberattack on a network or nodes such as information terminals and servers existing on the network (each of the devices that make up the computer network), conducted by white hackers. The test is to reveal what actions can be accomplished against targeted information resources.
