MTI Journal
MTI Journal.22
Initiatives for Ship Cybersecurity and Standardization of Ship-to-Shore Communication
Kana Wakaumi
Researcher, Maritime and Logistics Technology Group*
*The job title is as of July 26, 2023
I joined MTI in April 2020 and have been working on ship cybersecurity and the standardization of efficient data communication between ships and shore.
Background: Current State of the Maritime Industry
With the development of satellite communications in recent years, the constant connection of ships to the Internet has become widespread. As a result, the sharing of data between ships and shore has also increased rapidly for the purpose of such as monitoring voyage data on shore. While the sophistication of the environment surrounding ships has improved operational efficiency, two significant challenges have emerged: (1) an increased risk of ships being exposed to cyber-attacks, and (2) a growing demand for safe and efficient data communication between ships and shore. In fact, cyber-attacks against the maritime industry have been on the rise in recent years, and it is essential to take countermeasures. In the worst-case scenario, a ship that suffers a cyber-attack may have its operation taken over, running aground, or colliding with other ships, posing serious threats to the lives, safety of crew members, cargo, and the environment.
Regarding the challenge (2), the communication status of ships varies depending on the route, and stable and high-speed satellite communication is not yet common. Therefore, there is a need for standards for communication between ships and shore that cater to the unique characteristics of such ships.
Industry Trends in Ship Cybersecurity
Considering the current situation and the risks described above, security regulations in the maritime industry have been gradually strengthened. The first significant development occurred in the 98th session of the International Maritime Organization’s Maritime Safety Committee (MSC) in June 2017. Shipowners and operators were recommended to implement thorough cyber risk management measures within their Safety Management System (SMS) based on the SOLAS International Safety Management Code before the first annual inspection of compliance certificates after January 1, 2021. In response to this resolution, various classification societies and organizations issued cybersecurity rules and guidelines for ship operations to prepare for the law’s implementation in 2021. In response to this resolution, each classification societies and other organizations issued cybersecurity rules and guidelines for ship operations in preparation for the implementation of the recommendation in force in 2021. The second major development took place in April 2022 when the International Association of Classification Societies (IACS) issued Unified Requirements (UR) E26 (Cyber resilience of ships) and E27 (Cyber resilience of on-board systems and equipment) to establish and operate cyber-resistant ships. As a result, for ships contracted for construction on or after January 1, 2024, maritime equipment manufacturers, shipyards, and operators are required to ensure resilient ships where both IT and OT equipment are securely integrated into the ship’s network. Additionally, maritime equipment manufacturers must guarantee the security of individual onboard equipment. Consequently, security measures that were once considered “recommendations” in the past few years have now become “requirements”, and regulations have been strengthened.

Regulatory situation for ship cybersecurity
Ship Cybersecurity Measures: ConOps Creation
NYK has been collaborating with other companies to strengthen ship cybersecurity. From 2020 when I joined MTI to 2021, we first organized and compared NYK’s situation and ideals of ship cybersecurity from the aspects of People, Process, and Technology. We held discussions with each person concerned about the necessary organization, roles, and policies for NYK, as well as the ideal monitoring technology. Based on these discussions, we summarized the concept of operations (ConOps) for NYK’s ship cybersecurity*1.
Since then, we have been building an organization and technology to constantly monitor ships based on the ConOps. I have been involved in the entire process of ConOps creation and development, from the beginning to the implementation of the contents described in ConOps. This has been such an exciting experience, and I feel rewarded to see the plans created in ConOps being implemented in collaboration with stakeholders.
Ship Cybersecurity Measures: Technology Verification
The National Institute of Standards and Technology (NIST) Cybersecurity Framework, widely referenced as a guideline for cybersecurity measures, recommends taking security actions on five axes: Identify, Protect, Detect, Respond, and Recover. By implementing measures across the axes of People, Process, and Technology as described above, security can be strengthened comprehensively.
To effectively “Identify” threats and vulnerabilities on ships based on the NIST axis, it is essential to understand the current situation, including onboard equipment information and equipment connections. Therefore, we examined the usefulness of network diagrams and inventory creation tools available in the market to automatically gather this information. Specifically, we visited multiple ships, used these tools, and compared the results they generated with the actual equipment and network conditions on the ships to assess their accuracy. Throughout this activity, we gained insights into ships’ structures and observed the crews’ operations, which deepened my understanding of onboard perspectives and crew activities that can contribute to future projects.

One of the ships that we visited – VLCC (Very Large Crude Oil Carrier) TAGA

During tool verification on a ship’s bridge
From the perspective of “Detect” abnormalities, we also verified the monitoring tool for OT equipment. Onboard OT equipment is crucial for controlling the operation of ships, such as navigation and engine equipment. During this verification, we connected the tool to an environment simulating the ship’s operating system and conducted “passive monitoring” to listen the communication without affecting important systems. We assessed the tool’s performance when detecting abnormalities and gained valuable insights into these monitoring tools. For instance, the communication was visualized in real-time, allowing us to check protocols and devices with high or low communication on a single screen. By setting up policies in the tool and configuring notification accordingly, we received alerts for abnormalities and recommended countermeasures. Through this verification, we detected abnormalities that would have gone unnoticed without monitoring and confirmed the effectiveness of the tool. Monitoring of OT devices will be required by IACS in the future, and this experience has provided us with valuable knowledge about the progress of OT countermeasures to meet future demands.
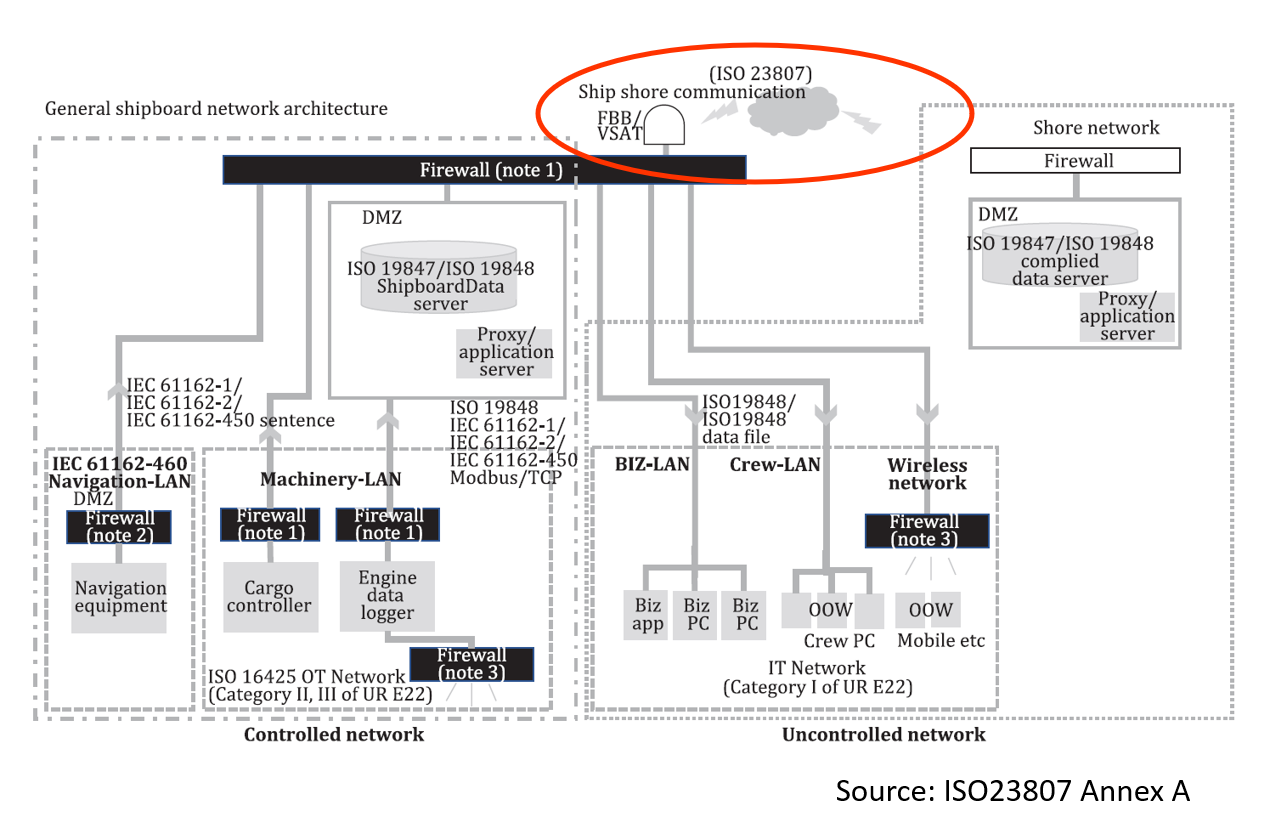
Standardization of Ship-to-Shore Communication ISO23807
As mentioned above, while the sharing of data between ships and shore has increased rapidly, file sharing between ships and shore has mainly relied on the method of attaching files to e-mails, resulting in the following problems*2.
- In slow ship-to-shore communication, large files cannot be delivered effectively.
- Repeated retransmissions over unstable satellite links cause delays in other business e-mails.
- Unsent problem due to outdated domains when changing communication providers.
- Security issues for critical files, and so on.
NYK/MTI have been working to resolve these issues through a strategic partnership with Dualog*3. Based on the results obtained through these activities, we worked to establish ISO23807, a new standard for ship-to-shore data communications.
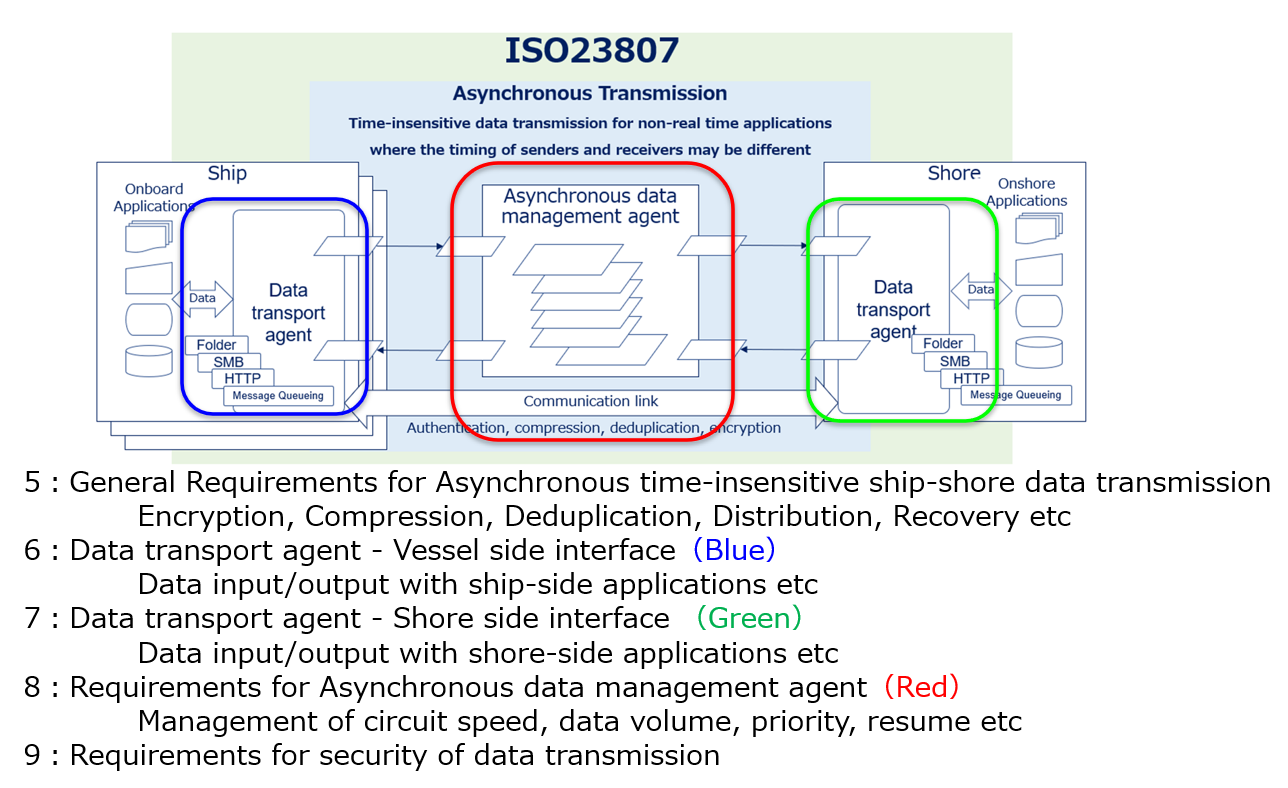
This standard defines the general functional requirements for stable, efficient, and secure file sharing between ships and shore. Its main scope is to ensure stable transmission of ship IoT data collected by the ISO 19847 ship-to-shore data server from ships to shore. Additionally, it is intended to be used for B2B (business-to-business) file exchange related to ship operations, such as sharing business files from ship management companies to management ships. As automation and autonomy of ship-to-ship equipment increase, software updates and AI algorithm updates will occur, and the need to reliably and securely distribute relatively large amounts of data from shore to operating ships will increase and become more critical. We believe that data exchange using this standard, rather than sending files via e-mail attachment, will be more effective in meeting these needs.
This standard outlines the general and security requirements for asynchronous data transmission between ships and shore, the functional requirements for ship-side and shore-side data transmission agents, and the functional requirements for asynchronous data management agents.
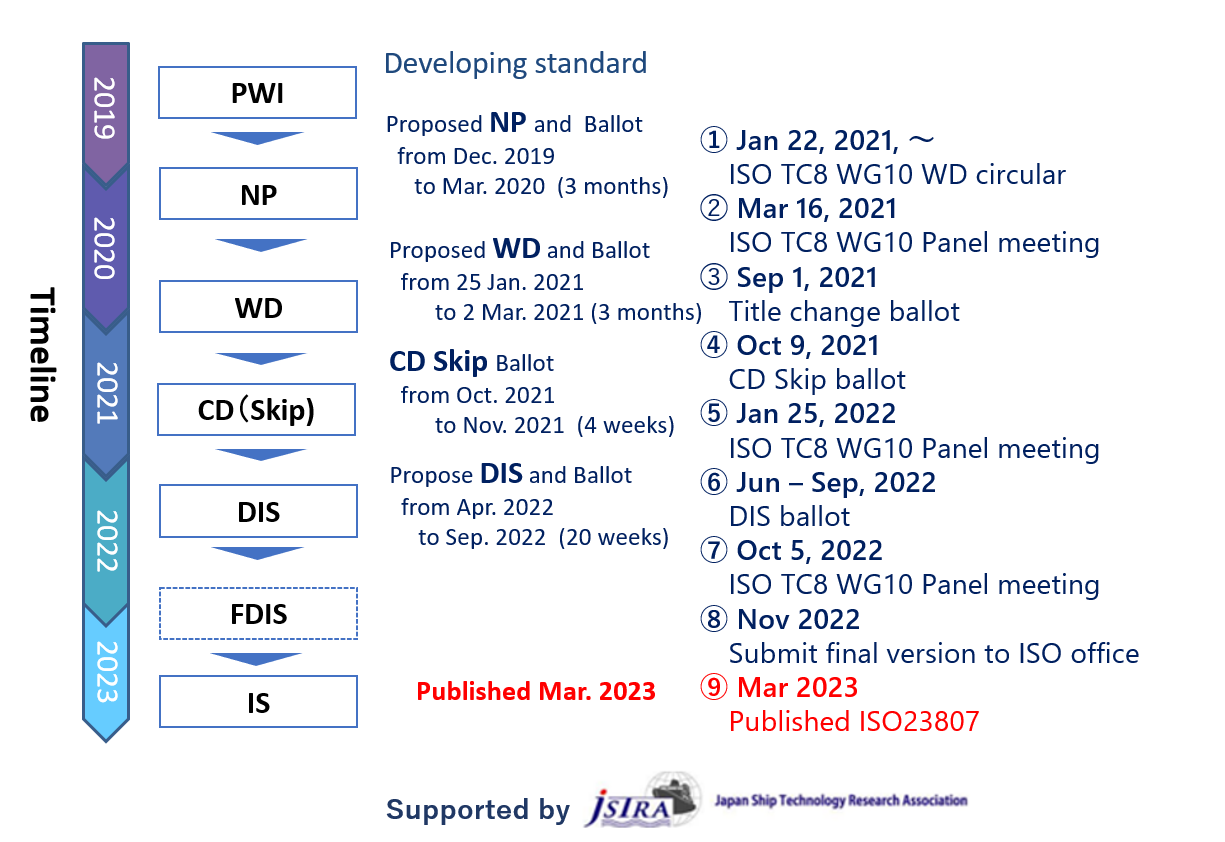
Efforts to standardize this protocol began in 2019. Following the ISO standard development process, it was officially standardized as ISO23807 in March 2023 after undergoing several rounds of discussions with experts from relevant countries at each step. During the meetings, the content of this standard was thoroughly scrutinized, and discussions were held regarding its classification and compatibility with surrounding standards. It was a highly valuable experience in my career that can be applied to future projects as well.
The Future of Ship-to-Shore Communication and Ship Cybersecurity
In the future, as satellite communications become more advanced and faster, the risk of ships being exposed to cyber incidents will increase further due to the growing demand for ship-to-shore communications. As we continue to deploy and utilize the stable, efficient, and secure ship-to-shore file sharing system established in ISO23807 on our ships, it will be essential to strengthen the ship’s cybersecurity measures.
Currently, NYK is implementing security measures for onboard IT equipment, building integrated monitoring measures for the entire fleet of onboard IT equipment, and investigating measures for onboard OT equipment. In close cooperation with shipyards and maritime equipment manufacturers, we will continue to enhance cybersecurity measures for ships to ensure the safe operation of our ships.
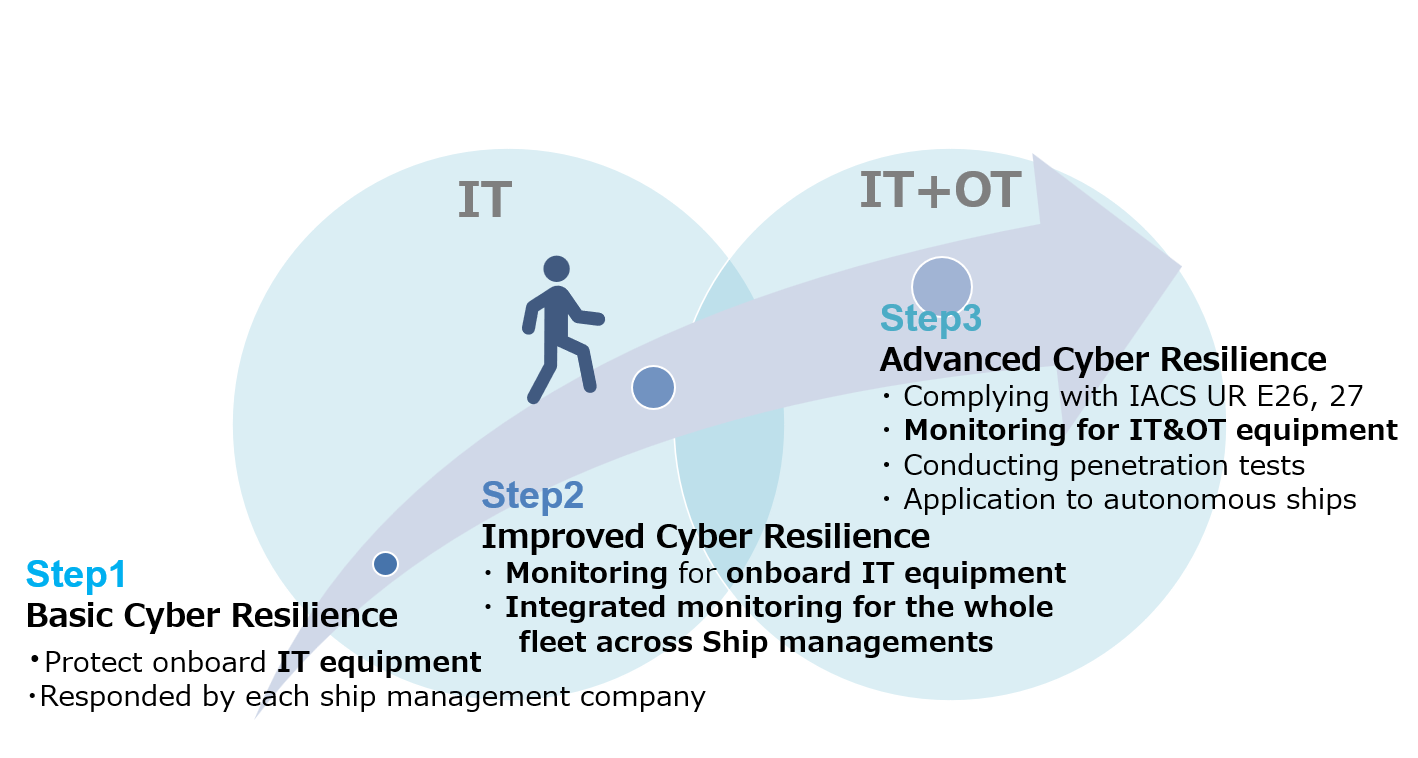
NYK Ship Cybersecurity Roadmap

With members of the crew, management company, and manufacturer on completion of the ship visiting work (she is on the far right)

Dualog, during their visit to the MTI office (she is third from the right)
*1 A document describing the characteristics of the system from users’ perspectives. It is used to communicate the quantitative and qualitative system characteristics to all stakeholders. It describes the organization, its mission, and its goals from an integrated systems perspective. (IEEE Guide for Information Technology – System Definition – Concept of Operations (ConOps) Document)
*2 The data sender (ship/shore) can execute and complete the data transmission request and move on to the next work process, regardless of the connection status of the ship/shore communication or the reception readiness status of the destination.
*3 Press releases on collaboration with Dualog:
Press release on May 31, 2017: NYK and Dualog Enters into Strategic Partnership for Joint Innovation